Building cyber resilience in the quantum era: the wake-up call from China
In May 2025, a significant development shook the global cybersecurity community: researchers in China used a commercial quantum computer to break RSA-90 encryption. While this is a relatively small key size by today’s standards, it marks the first real-world demonstration of quantum technology undermining classical encryption. The message is clear—the quantum era is no longer a distant future; it has begun. This milestone reinforces the urgency of building cyber resilience in anticipation of the transformative and disruptive power of quantum computing.
What is quantum computing?
Unlike classical computers, which use bits (0s and 1s) to process information, quantum computers use qubits, which can exist in multiple states simultaneously due to a phenomenon called superposition. Additionally, quantum entanglement allows qubits to be correlated with each other instantaneously over any distance, leading to exponentially faster computations for certain problems. These capabilities make quantum computers particularly adept at solving complex mathematical problems that underpin modern cryptographic systems.
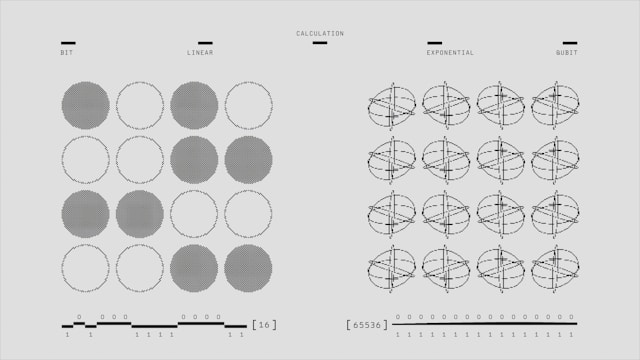
The cybersecurity threats posed by quantum computing
Quantum computers can solve complex mathematical problems far faster than classical systems—especially those problems that are foundational to modern cryptography.
As Dario Gil, Director of IBM Research, stated:
“Quantum computing is expected to unlock innovations that will fundamentally reshape industries, from logistics to pharmaceuticals, and lead to new breakthroughs in artificial intelligence.”
However, these capabilities also present serious cybersecurity risks.
The primary cybersecurity concern associated with quantum computing is its ability to break widely used encryption algorithms. Most current cryptographic methods rely on mathematical problems that are infeasible for classical computers to solve within a reasonable timeframe but could be efficiently cracked by quantum computers.
- Breaking public-key encryption: Public-key cryptographic protocols, such as RSA, ECC (Elliptic Curve Cryptography), and Diffie-Hellman, rely on problems like integer factorization and discrete logarithms, which are extremely difficult for classical computers to solve. However, Shor’s algorithm, a quantum algorithm, can efficiently solve these problems, rendering such encryption methods obsolete.
- Compromising secure communications: Encryption protocols such as TLS (used for HTTPS websites), email encryption, and secure messaging rely on public-key encryption. If quantum computers become sufficiently powerful, they could decrypt sensitive communications, jeopardizing personal privacy and national security.
- Threat to cryptographic hash functions: Cryptographic hash functions, such as SHA-256, are essential for data integrity, digital signatures, and blockchain technology. Quantum algorithms like Grover’s algorithm can significantly speed up hash function computations, weakening their security.
Global developments: a race for quantum supremacy
Nations around the world are intensifying efforts to develop quantum computing technologies, with China emerging as a key player alongside the U.S. While the U.S. has been at the forefront of research in post-quantum cryptography and standardization, China has made notable strides, particularly in applied quantum technologies like secure communications.
In late 2024, China introduced the “Xiaohong-504” superconducting chip, powering a 504-qubit quantum computer called Tianyan-504. This places China among the few countries capable of deploying large-scale quantum systems, and reinforces its position in the quantum arms race—especially in applications like secure communications and national-scale quantum networks.
With countries like China making rapid advancements, the urgency for others, including the U.S. and Europe, to prioritize the development of quantum-resistant solutions has never been higher. Cybersecurity professionals are actively developing quantum-resistant solutions to ensure resilience in the quantum era. These efforts include Post-Quantum Cryptography (PQC). These algorithms are designed to be resistant to quantum attacks while remaining efficient for classical computers.
The National Institute of Standards and Technology (NIST) is leading an initiative to standardize quantum-resistant cryptographic algorithms. As part of this effort, NIST launched a Post-Quantum Cryptography Standardization Project in 2016, inviting researchers from around the world to propose and analyze new cryptographic algorithms capable of withstanding quantum threats. The process involves multiple rounds of evaluation, testing the security, performance, and practicality of the proposed algorithms. In 2022, NIST announced four finalist algorithms—CRYSTALS-Kyber, CRYSTALS-Dilithium, Falcon, and SPHINCS+—which are now being refined for final standardization. These new cryptographic standards will serve as the foundation for future cybersecurity defenses against quantum threats.
Building a quantum-resilient future
While the timeline for fully capable quantum computers is still debated, the recent breakthrough in China shows that the window to prepare is shrinking. Retrofitting existing systems with quantum-safe encryption is a massive undertaking that will take years, possibly decades. That work must start now.
To build quantum resilience, organizations must:
-
Inventory and classify cryptographic assets
-
Pilot hybrid encryption systems combining classical and quantum-safe methods
-
Monitor standardization efforts and integrate new algorithms early
-
Collaborate across borders to ensure global security standards evolve together
Quantum computing represents a double-edged sword. It has the potential to unlock new discoveries and efficiencies, but it also threatens to dismantle the cryptographic systems that underpin our digital world. The recent Chinese experiment is a clear warning: waiting is no longer an option. Governments, industries, and cybersecurity leaders must act now to transition to post-quantum cryptographic infrastructures—before theoretical risk becomes irreversible reality.
Looking to invest in cybersecurity with confidence?
At ACK3, we help public and private organizations strengthen their digital security with tailored solutions, cutting-edge technology, and expert cyber defense teams.